DRYAD
|
|
The DRYAD Numeral Cipher/Authentication System (KTC 1400 D) is a simple, paper cryptographic system currently in use by the U.S. military for authentication and for encryption of short, numerical messages. Every unit with a radio is given a set of DRYAD code sheets. A single sheet is valid for a limited time (e.g. 6 hours), called a cryptoperiod.
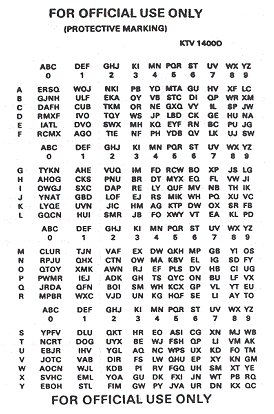
A DRYAD code sheet contains 25 lines or rows indexed by the letters in a column on the left of the page. Each row contains a random permutation of the letters A thru Y. The letters in each row are grouped into 10 columns labeled 0 thru 9. The columns under 0, 1, 2 and 5 have more letters that the other digits, which have just two each.
DRYAD is used in two modes, authentication and encryption. For authentication, a challenging station selects two letters from A thru Y at random. The challenged station uses the first letter to select a row in the currently active DRYAD page. The second letter is then located in the row and the letter below it is the response. (One obvious problem here is that an enemy trying to penetrate a network has one chance in 25 of guessing the right response. On the other hand, a two character response would reduce the useful life of a page.)
The second mode is used to encrypt short numeric information, like map coordinates or a new radio frequency. The coder selects two letters at random. The first selects a row in the current active page. The second letter is used as in the authentication mode, except the letter to the right is selected and called the "SET LETTER."
Numbers are enciphered one digit at a time. A ciphertext letter is chosen from the selected row in the column under the plain text digit. If the digit occurs more than once in the number, the coder is instructed to choose a different letter in the same column. All the digits in a single plaintext number are encoded from the same row. (There is also a provision for encoding letters associated with map grid coordinates.)
While crude, this system has the advantage of being fast, relatively easy and not requiring even a pencil. The presence of more cipher-text columns under the digits 0, 1 and 5, is apparently intended to make ciphertext frequency analysis more difficult. But much of the security comes from keeping the cryptoperiod short.